Secure Communication
The first applications of a quantum internet are expected to be ones that better secure our communication.
Secure communication in critical infrastructures
Our modern society relies heavily on the continuous, reliable and safe exchange of information sent over the classical internet. Every time you send a message via email or WhatsApp, every time you make a purchase on a website or upload your data to a tax organization, your information is sent via the classical internet; you trust that your information arrives and is not stolen by a third party. Much of the critical infrastructures in our society also depend on secure communication. Bridges, power plants, transportation systems, the banking system and governmental services such as the police and fire brigade, all need to exchange information for their smooth operation. Substantial interception of that information by hackers or adversaries would soon jeopardize the trust we have in society. Consider, for instance, a situation in which you cannot rely anymore on your email, electronic money transfers, the updates that companies send to our computers, or the equipment in hospitals or chemical plants.
Much of the information that is sent over the classical internet is currently made secure by keys that are created with encryption techniques that also exchange information over the classical internet. This allows hackers and adversaries to intercept that encryption information, and then to attempt breaking the encryption by finding the key. They can do so with decryption algorithms running on classical computers or, in the future, with algorithms that run on quantum computers. And once hackers have the key, the encrypted communication over the classical internet is no longer secure.
Quantum internet can block these decryption attempts by hackers and adversaries. It allows for the use of quantum encryption techniques that exchange information for creating keys safely over the quantum internet. With these keys communication that is sent on the classical internet can then be made secure again. The main quantum encryption technique is quantum key distribution (see page 17).
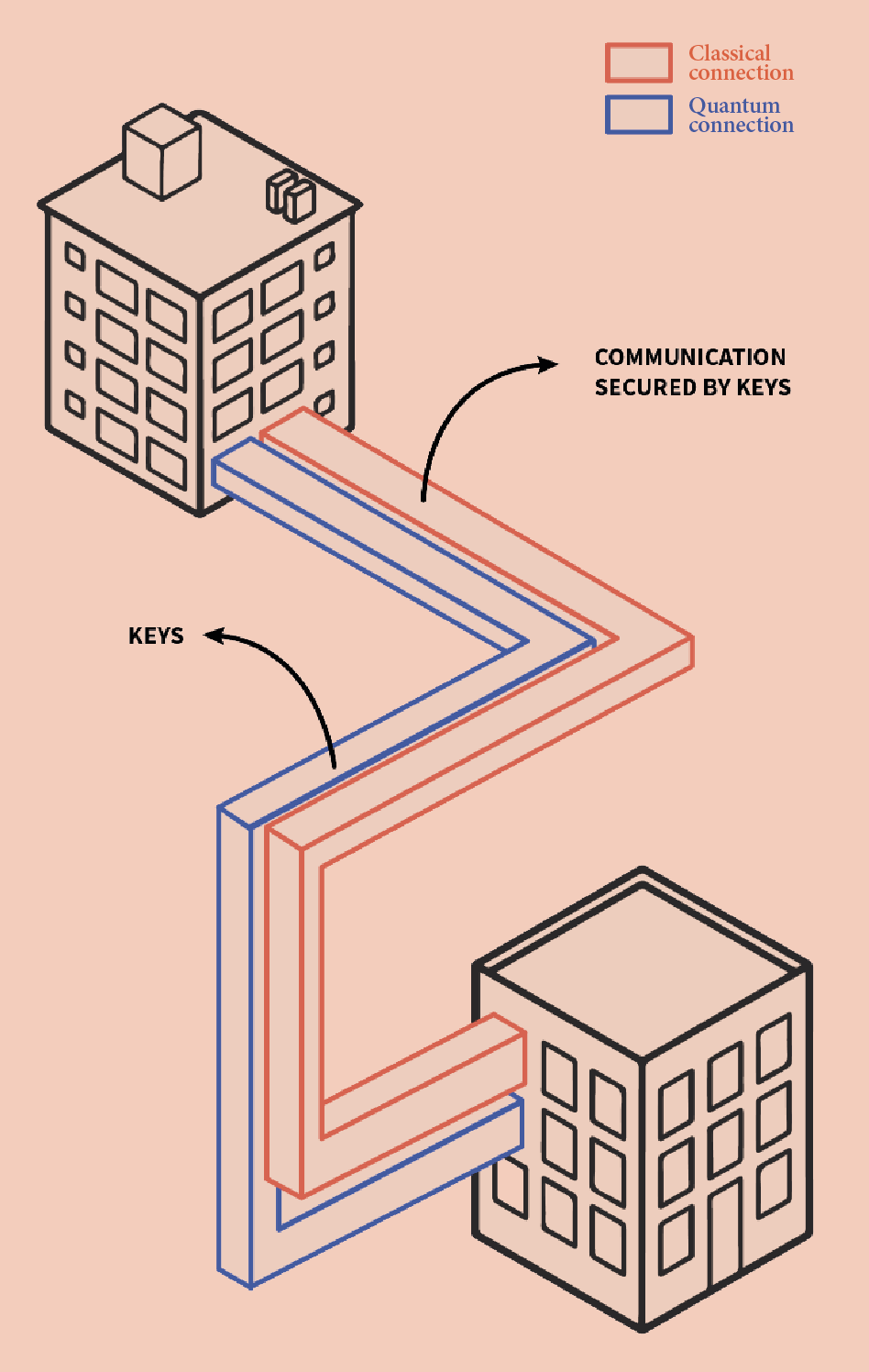
The first applications of quantum key distribution
It is to be expected that the first communication that is secured with quantum key distribution is communication between academic institutions, state institutions and between companies. The usual classical internet connections between these institutions and companies are then supplemented with quantum internet connections. And the quantum internet connections are used to generate encryption keys for securing communication over the classical internet. Later applications may enable securing the communication of individuals. For example, when banks connect their ATMs to the quantum internet, the communication between individuals and banks can be secured by quantum key distribution (see the next page).
Quantum key distribution already in use
Quantum key distribution is already in use. In Switzerland, quantum key distribution is used to secure the network between the places where the votes of elections are counted and stored. Quantum key distribution is also already in use in the Netherlands. In 2016, KPN established a safe network between datacenters in the Dutch cities of The Hague and Rotterdam by using quantum key distribution. In the future, quantum key distribution is expected to be used in more cases, like for auctions, elections or contract negotiations.
Types of encryption
Cryptography is the field that studies how to secure information. The security goals of the end users can be different and relate to secrecy, data integrity, authentication and non-repudiation.
Today’s cryptography
Most of today’s cryptographic protocols are secure through hard mathematical problems like the integer factorization problem, the discrete logarithm problem or the elliptic-curve discrete logarithm problem. This is the case for the most popular public key cryptosystems. However, some of these problems are not hard for quantum computers. In particular, a quantum computer implementing Shor’s algorithm can solve the examples above exponentially faster than a classical one. Hence, while some instances of these problems cannot be tackled by today’s most powerful supercomputer, a powerful quantum computer could tackle them and, in consequence, break public key cryptosystems.
Quantum cryptography
Quantum cryptography studies how to secure information leveraging quantum resources. The most important example is quantum key distribution (see page 17). It provides secure keys to distant parties that can, in turn, be used to achieve fully secure communication. When exchanging keys through quantum key distribution, eavesdroppers are detected immediately, and the exchange can be aborted.
Classical post-quantum cryptography
(also referred to as quantum-proof or quantum-resistant cryptography)
Classical post-quantum cryptography proposes classical cryptosystems that are expected to be secure against attacks from quantum computers. One example is symmetric encryption schemes, which is only moderately affected by quantum computers. A quantum computer running Grover’s algorithm can search for the secret key faster than a classical computer, but the speedup is moderate. It is believed that by doubling the key lengths current symmetric cryptosystems will remain safe even against quantum computers. Other solutions are lattice-based cryptography, hash-based cryptography, code-based cryptography, multi-variate cryptography and supersingular isogeny-based cryptography.
References
www.newscientist.com/article/dn12786-quantum-cryptography-to-protect-swiss-election/
KPN (2016). KPN to implement quantum encrypted connection (QKD).